One of the most popular and widely used web servers for Java is Apache Tomcat. It’s small, simple to install, and very nice for building Java web applications. It can also be used to build slightly more sophisticated applications than the conventional JSP application online, as it can include JSF implementations such as MyFaces, Primefaces, RichFaces and others (standard library, defined in J2EE for developing dynamic web applications using Java) .
All of this is very beneficial, and in fact, many web application developers use it in their teams so they can develop quickly and can focus on what really matters to them: making sure that the logic of their Java classes and pages works as it should. All this is very beneficial. It really is that simple… a software developer normally doesn’t care about the security of the Tomcat server that he has installed on the computer that his employer has provided him with. In fact, the concept of security is so foreign to him that it doesn’t even cross his mind very often. “Pure Java” HTTP web server environments are available through the Apache Tomcat server, which incorporates Jakarta Servlet, Jakarta Expression Language, and WebSocket technologies. These technologies allow Java code to run in these environments. Because of this, it is a frequently chosen choice among developers who want to use Java to build online applications.
Apache Tomcat versions up to and including 8.5.85/9.0.71/10.1.5/11.0.0-M2 have been determined to have a vulnerability that has been rated problematic (application server software). An unidentified feature of the component known as the RemoteIpFilter Handler is broken as a result of this bug. Tampering with unknown input results in a vulnerability involving insecure transmission of credentials. The username and password are not adequately protected when sent from the client to the server through the login pages, which do not use adequate security measures.
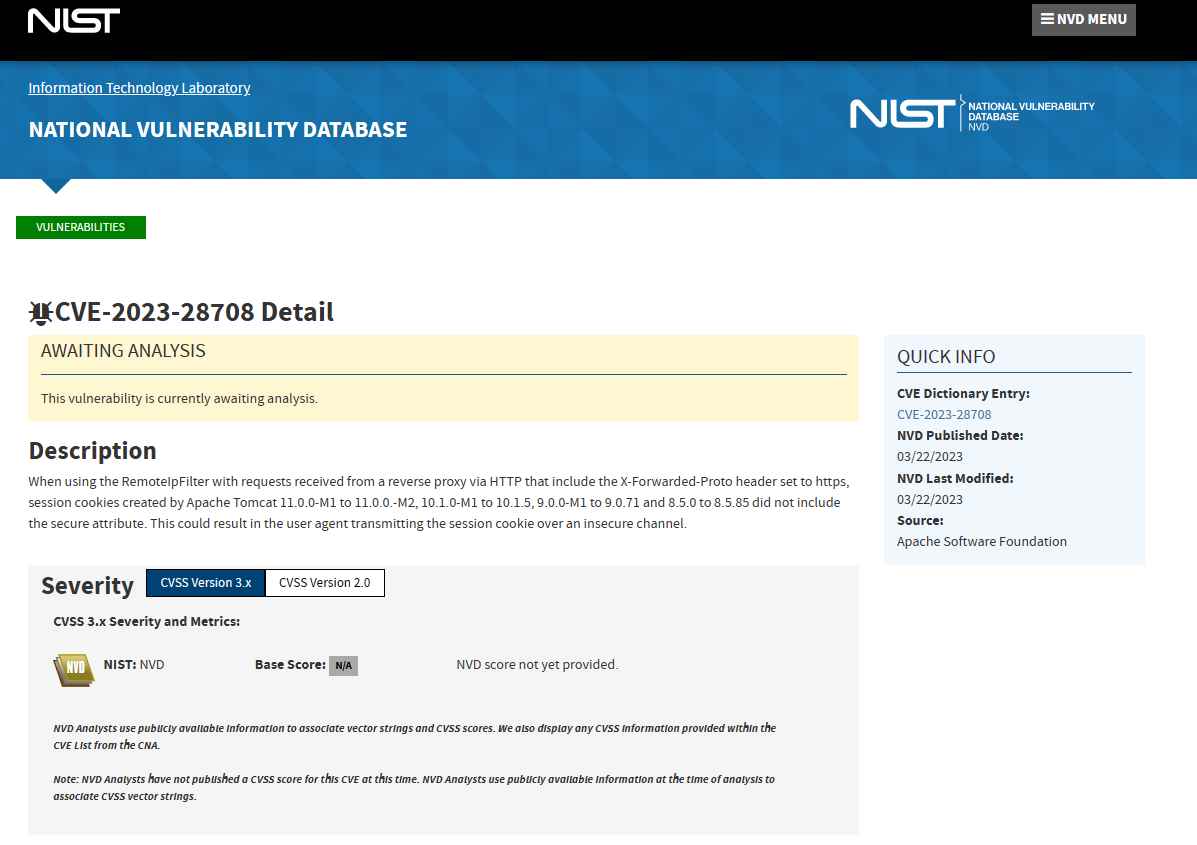
Session cookies generated by Apache Tomcat versions 11.0.0-M1 to 11.0.0.-M2, 10.1.0-M1 to 10.1.5, 9.0.0-M1 to 9.0.71 and 8.5.0 to 8.5.85 do not The secure attribute is included when used in conjunction with requests received from a reverse proxy over HTTP and had the X-Forwarded-Proto header set to https. Because of this, the user agent could send the session cookie over an unsecured connection. Therefore, this could be dangerous.
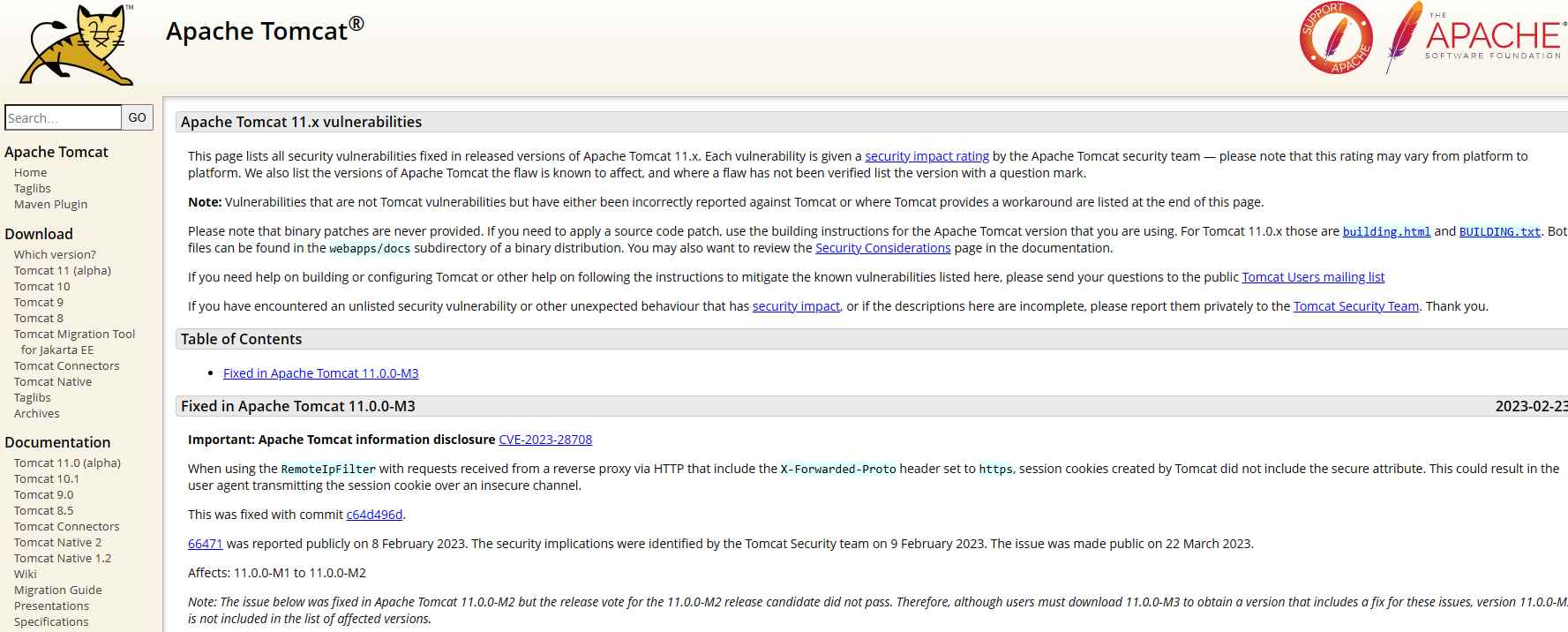
The vulnerability was disclosed on March 22, 2023. The advisory is now available for download at enlists.apache.org, where it is also shared. As of March 21, 2023, this vulnerability has been assigned the identifier CVE-2023-28708. There is no technical description or exploit that is easily accessible to the public. The method of attack was given the designation T1557 by the MITER ATT&CK project.
This vulnerability can be fixed by updating to version 8.5.86, 9.0.72, 10.1.6, or 11.0.0-M3, respectively.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He has also worked for security companies such as Kaspersky Lab. His daily work includes investigating new malware and cybersecurity incidents. He also has a deep level of knowledge in mobile security and mobile vulnerabilities.
Send news tips to [email protected] or www.instagram.com/iicsorg/
You can also find us on Telegram www.t.me/noticiasciberseguridad
