2024-07-19 21:41:47
In the wake of the shock of events, there is widespread chaos in various sectors around the world due to a global technological disruption caused by a faulty CrowdStrike software update. The incident, which disrupted systems running Microsoft Windows, grounded flights, disrupted hospitals, and halted many business operations, highlighting the critical dependencies of cybersecurity infrastructure in the modern digital age.
IRISH: ADULT UPDATES
The outage was caused by a single content update for Windows released by CrowdStrike, a leading cyber security company. There was a flaw in the update that caused massive failures in many systems, leading to a domino effect of IT outages around the world. It had a profound impact, affecting various sectors, from airlines and banks to hospitals and individual computer users.
IMMEDIATE AND SUBSEQUENT EFFECTS
The immediate consequences were serious and widespread:
- Airlines : Thousands of flights were cancelled, causing major delays and disruption at airports around the world.
- Hospitals : Medical facilities faced critical operational challenges when their IT systems went offline, complicating patient care and medical procedures.
- Financial institutions : There was significant disruption in banks and other financial institutions that affected daily transactions and operations.
- Media : Many media organizations were able to gain access to their networks, hampering news dissemination and media operations.
The interconnected nature of global IT infrastructures exacerbated the chaos, highlighting vulnerabilities that could lead to such widespread crises.
CrowdStrike, along with Microsoft, is working hard to resolve the issue. Below is a step-by-step explanation of how to identify and evaluate affected systems using specific queries in the Advanced Event Search.
STEP 1: DETERMINE THE RELEVANT CHANNEL FILE
The first step involves running a query to identify the affected channel file, which will help determine the scope of affected systems. Run the following query in Advanced Event Search with the search window set to seven days.
#event_simpleName=ConfigStateUpdate event_platform=Win | regex( “|1,123,(?.*?)|”, field=ConfigStateData, strict=false) | parseInt(CFVersion, radix=16) | group at[cid]function =([max(CFVersion, as=GoodChannel)])) | ImpactedChannel:=GoodChannel-1 | join(query={#data_source_name=cid_name | groupBy([cid]function=selectLast(name), limit=max)}, field=[cid]include = name, mode = left)
Note the value in the “ImpactedChannel” column.
This number
Explanation:
- Filter Events : The query filters events with the name ConfigStateUpdated on a Windows platform.
- Excerpt version – Uses a regular expression to extract the configuration file version of the event data.
- Analysis version – The extracted version number is parsed as an integer.
- Grouping by customer identification (cid) : Versions are grouped by client ID and the highest version number is identified.
- Determine the affected channel – The concerned channel file is found by subtracting one from the highest version number.
Note the value in the “ImpactedChannel” column. This value will be used in the next step and is usually around 30 for Falcon tenants.
STEP 2: A DETAILED INQUIRY RULE TO IDENTIFY SYSTEMS THAT ARE BROKEN
Once the affected channel file is identified, the next step is to run a more detailed query to identify the affected systems during the critical impact window.
Consultation to identify impact systems:
// Get ConfigStateUpdate and SensorHeartbeat events #event_simpleName=/^(ConfigStateUpdate|SensorHeartbeat)$/ event_platform=Win // Narrow search to Channel File 291 and extract version number; accept all SensorHeartbeat events | case { #event_simpleName=ConfigStateUpdate | regex( “|1,123,(?.*?)|”, field=ConfigStateData, strict=false) | parseInt(CFVersion, radix=16); #event_simpleName=SensorHeartbeat | rename ([[@timestamp, LastSeen]]); } // Restrict the results to the hosts that were online during the affected time window | case { #event_simpleName=ConfigStateUpdate | @timestamp>1721362140000 AND @timestamp < 1721366820000 | CSUcounter:=1;
#event_simpleName=SensorHeartbeat | LastSeen>1721362140000 AND LAST SEEN<1721366820000 | SHBcounter:=1;
*;
}
| default(value="0", field=[CSUcounter, SHBcounter])
// Make sure both ConfigState update and SensorHeartbeat have happened
| selfJoinFilter(field=[cid, aid, ComputerName], where=[{ConfigStateUpdate},
{SensorHeartbeat}])
// Aggregate results
| groupBy([cid, aid], function=([{selectFromMax(field="@timestamp",
include=[CFVersion])}, {selectFromMax(field="@timestamp", include=[@timestamp])
| rename(field="@timestamp", as="LastSeen")}, max(CSUcounter, as=CSUcounter),
max(SHBcounter, as=SHBcounter)]), limit=max)
// Perform check on selfJoinFilter
| CFVersion=* LastSeen=*
// ////////////////////////////////////////////////////////// //
// UPDATE THE LINE BELOW WITH THE IMPACTED CHANNEL FILE NUMBER //
// ////////////////////////////////////////////////////////// //
| in(field="CFVersion", values=[0,31])
// Calculate time between last seen and now
| LastSeenDelta:=now()-LastSeen
// Optional threshold; 3600000 is one hour; this can be adjusted
| LastSeenDelta>3600000 // Calculate the distance between last time and today | LastSeenDelta:=formatDuration(“LastSeenDelta”, precision=2) // Convert LastSeen time to human readable format | LastSeen:=formatTime(format=”%F %T”, field=”LastSeen”) // Enrich aggregate with aid_master data | aid=~match(file=”aid_master_main.csv”, column=[aid]) | aid=~match(file=”aid_master_details.csv”, column=[aid]include=[FalconGroupingTags, SensorGroupingTags]) // Convert FirstSeen time to human readable format | FirstSeen:=formatTime(format=”%F %T”, field=”FirstSeen”) // Move ProductType to human readable format and add formatting | $falcon/helper:enrich(field=Product Type) | release ([Time]) | default(value = “-“, field=[MachineDomain, OU, SiteName, FalconGroupingTags,
SensorGroupingTags], replaceEmpty=true) // Create conditions to check impact | case { LastSeenDelta > 3600000 | Details:=”OK: Last visible endpoint.”; CSUcounter=0 AND SHBcounter=0 | Details:=”OK: Endpoint did not receive a channel file during the crash window. The endpoint was offline.”; CSUcounter=0 AND SHBcounter=1 | Details:=”OK: Endpoint did not receive a channel file during the crash window. The endpoint was online.”; CSUcounter=1 AND SHBcounter=1 | Details:=”CHECK: The endpoint received a channel file during the crash window. The endpoint was online. The endpoint has not been seen online for the past hour.”; } // Create one final group For easier export to CSV | group at[cid, aid, ComputerName, LastSeen, CFVersion, LastSeenDelta, Details,
AgentVersion, aip, event_platform, FalconGroupingTags, LocalAddressIP4, MAC,
MachineDomain, OU, ProductType, SensorGroupingTags, SiteName,
SystemManufacturer,SystemProductName, Version]limit=max)
Explanation:
- Filter events – The query selects events with the names ConfigStateUpdate and SensorHeartbeat on the Windows platform.
- Extract and analyze a version – Extracts the configuration file version from the ConfigStateUpdate events and parses it as an integer.
- Identify the time window – Events occurring within the impact window are filtered (0400 – 0600 UTC July 19, 2024).
- Counter Indicators – Counters are set for systems that were online and the update was processed during the impact window.
- Accept the filters ConfigStateUpdate – Ensures that both SensorHeartbeat events have occurred for the same systems.
- Aggregated results – Returns the results, including the configuration file version and the last viewed timestamp.
- Check affected versions – Filter systems running the affected channel file version (CFVersion) identified above.
- Calculate delta time – Calculates the time since the systems were last seen and formats them for readability.
- Data enrichment – Applies additional data from master files and converts timestamps to human readable formats.
- Impact evaluation – Sets detailed status messages based on system update and online status during the impact window.
- Export results – Group the final results for easier export to CSV.
Important – Update the line with the file number of the concerned channel derived from Step 1:
Copy sql| sa (field = “CFVersion”, values =[0,31])
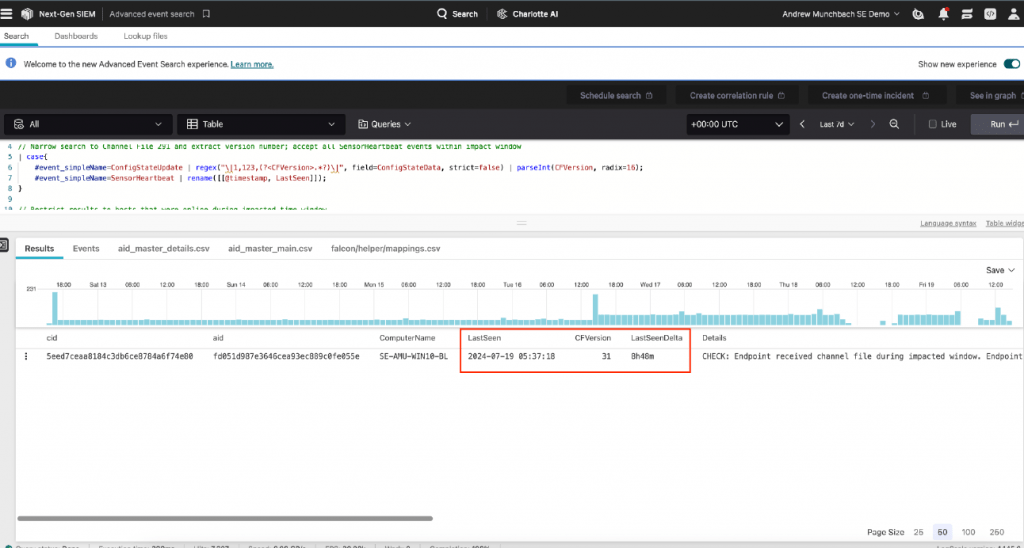
Adjust the time window if necessary by changing the threshold value. The default value is set to one hour (3600000 milliseconds). The result of this query will show the systems that were last reported to have run an affected version of the channel file 291 that was not last seen.
If the time interval of one hour is too long, it can be adjusted on line 26 of the query:
//Optional threshold; It is 3600000 hours
| Last Delta>3600000
The value is 3600000 hours in milliseconds. You can choose the portal that best suits your needs.
needs.
By following these steps and using the provided queries, you will be able to accurately assess and identify the systems affected by the recent CrowdStrike breach. This method ensures that all affected systems are evaluated and the necessary corrective actions are taken quickly to restore normal operations.

He is a recognized expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cybersecurity analyst in 2003. He works actively as an anti-malware expert. He also worked for security companies like Kaspersky Lab. He also has a deep level of knowledge of mobile security and mobile vulnerabilities.
Send news tips to [email protected] or www.instagram.com/iicsorg/
You can also find us on Telegram www.t.me/noticiasciberseguro
#Systems #Detect #CrowdStrike #Breach #OnPremise #Cloud #Environment

