vBulletin under Siege: Are Your Forums at Risk?
Table of Contents
- vBulletin under Siege: Are Your Forums at Risk?
- The Double threat: CVE-2025-48827 and CVE-2025-48828
- Silent Patches and Unpatched Systems: A Recipe for Disaster
- The Anatomy of the Exploit: How Attackers gain Control
- Exploitation in the Wild: Attacks Originating from Poland
- vBulletin’s Troubled Past: A History of Vulnerabilities
- What’s Next? The Future of vBulletin Security
- Mitigation Strategies: Protecting Your Forum
- The Future of Forum Security: A Call to Action
- Time.news Asks: Is Your vBulletin Forum at Risk? an Expert Weighs In
Is your online community built on vBulletin? If so, you might be sitting on a ticking time bomb. Two critical vulnerabilities have surfaced, and one is already being exploited in the wild, potentially handing attackers the keys to your server.
The Double threat: CVE-2025-48827 and CVE-2025-48828
Thes aren’t your run-of-the-mill bugs. Tracked as CVE-2025-48827 (CVSS 10.0) and CVE-2025-48828 (CVSS 9.0), these flaws represent a severe threat. They involve an API method invocation issue and a remote code execution (RCE) vulnerability stemming from template engine abuse.
Fast Fact: A CVSS score of 10.0 indicates the most critical type of vulnerability, allowing attackers to fully compromise a system with minimal effort.
Affected versions include vBulletin 5.0.0 through 5.7.5 and 6.0.0 through 6.0.3,specifically when running on PHP 8.1 or later. This combination unlocks the exploit’s potential.
Silent Patches and Unpatched Systems: A Recipe for Disaster
While patches were likely released quietly last year (Patch Level 1 for 6.* and Patch level 3 for 5.7.5), many forum administrators haven’t upgraded. This leaves countless sites vulnerable to attack.
Expert Tip: Regularly updating your software, especially forum platforms like vBulletin, is crucial for maintaining security. Don’t wait for a major breach to take action.
The Anatomy of the Exploit: How Attackers gain Control
Security researcher Roman egidio (EgiX) meticulously detailed the exploit, revealing how vBulletin’s misuse of PHP’s Reflection API, combined with changes in PHP 8.1, allows attackers to invoke protected methods without proper authorization.
Crafted URLs and Template Engine Trickery
The attack chain involves crafting malicious URLs and exploiting template conditionals within vBulletin’s template engine. By injecting code using the vulnerable ‘replaceAdTemplate’ method, attackers bypass security filters.
Did you know? PHP’s Reflection API allows code to inspect and modify itself during runtime.While powerful, it can be a security risk if not handled carefully.
Remote Code Execution: The Ultimate Prize
The result? Full remote, unauthenticated code execution. Attackers gain shell access as the web server user (e.g., www-data on Linux), effectively owning the server.
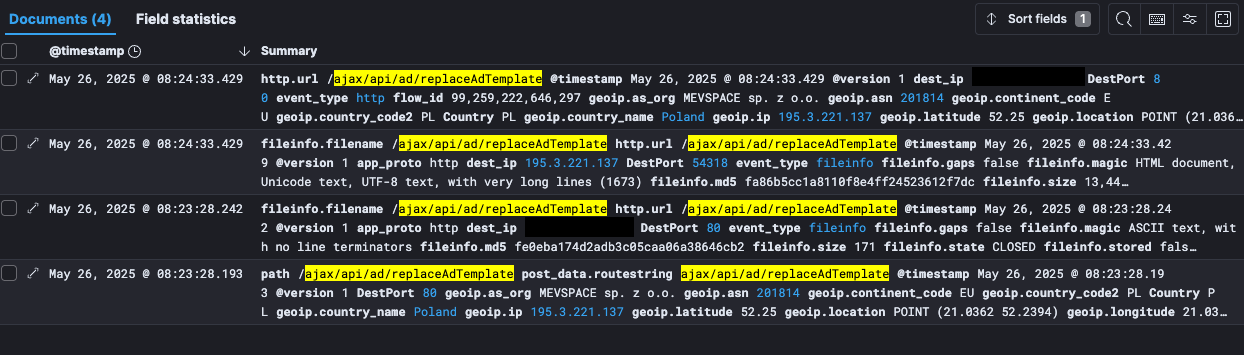
Exploitation in the Wild: Attacks Originating from Poland
Security researcher Ryan Dewhurst confirmed active exploitation, spotting attempts to exploit the ‘ajax/api/ad/replaceAdTemplate’ endpoint in honeypot logs. One attacker was traced back to poland, attempting to deploy PHP backdoors for executing system commands.
Source: blog.kevintel.com
While Dewhurst only observed exploitation attempts for CVE-2025-48827, the potential for chaining it to achieve full RCE is high. The availability of Nuclei templates since May 24, 2025, further lowers the barrier to entry for attackers.
vBulletin’s Troubled Past: A History of Vulnerabilities
vBulletin,a widely used commercial forum platform,has a history of security vulnerabilities. Its modular design, while offering adaptability, also creates a large attack surface.
Real-World Example: In the past,flaws in vBulletin have led to breaches of major forums,including Epic Games,resulting in the theft of sensitive user data.
This isn’t just a theoretical risk; it’s a pattern. The platform has been targeted repeatedly, leading to notable data breaches and reputational damage for affected communities.
What’s Next? The Future of vBulletin Security
Given the active exploitation and the severity of these vulnerabilities, what can we expect in the coming months?
Increased Attack Volume
With public proof-of-concept code readily available, we’re likely to see a surge in exploitation attempts. Attackers will target vulnerable vBulletin forums to install backdoors, steal data, or use them as launching pads for further attacks.
The Rise of Automated Exploitation
Expect to see automated tools and botnets incorporating these exploits. This will allow attackers to scan and compromise large numbers of vulnerable forums quickly and efficiently.
Focus on Data exfiltration
Compromised forums are a goldmine of user data, including usernames, passwords, email addresses, and private messages. Attackers will likely prioritize exfiltrating this data for sale on the dark web or for use in credential stuffing attacks.
Potential for Ransomware Attacks
While not yet observed, the possibility of ransomware attacks targeting vBulletin forums cannot be ruled out.Attackers could encrypt forum databases and demand a ransom for their release.
Mitigation Strategies: Protecting Your Forum
What steps can forum administrators take to protect their communities?
Immediate Patching
The most critical step is to apply the latest security updates for your vBulletin installation. If you’re running a vulnerable version, upgrade to version 6.1.1 or later promptly.
Web Application Firewall (WAF)
Implement a WAF to filter out malicious traffic and block exploitation attempts. Configure the WAF to specifically protect against the CVE-2025-48827 and CVE-2025-48828 vulnerabilities.
Intrusion detection and Prevention Systems (IDS/IPS)
Deploy IDS/IPS solutions to monitor network traffic for suspicious activity and automatically block known attack patterns.
Regular Security Audits
Conduct regular security audits of your vBulletin installation to identify and address potential vulnerabilities before they can be exploited.
User Education
Educate your users about phishing attacks and other social engineering tactics.Encourage them to use strong, unique passwords and to be wary of suspicious links or attachments.
The Future of Forum Security: A Call to Action
The vBulletin vulnerabilities serve as a stark reminder of the importance of proactive security measures. Forum administrators must prioritize patching, implement robust security controls, and stay informed about emerging threats. The future of online communities depends on it.
Time.news Asks: Is Your vBulletin Forum at Risk? an Expert Weighs In
Keywords: vBulletin vulnerability, vBulletin security, CVE-2025-48827, CVE-2025-48828, forum security, remote code execution, RCE, patch vBulletin
Time.news: We’re seeing reports of critical vulnerabilities affecting vBulletin forums. Dr. Anya Sharma,a leading cybersecurity researcher specializing in forum software security,joins us today to shed light on the situation. Dr. Sharma, welcome. can you paint a picture of the severity of these vBulletin vulnerabilities?
Dr. Anya Sharma: thanks for having me. The current situation with vBulletin is indeed concerning. We’re talking about two severe vulnerabilities, CVE-2025-48827, which carries a maximum CVSS score of 10.0, and CVE-2025-48828, with a score of 9.0. These aren’t minor annoyances; they represent a serious risk of complete server compromise.The 10.0 score essentially means an attacker can gain full control with relative ease, especially if the forum is running vulnerable versions on PHP 8.1 or later.
Time.news: The article mentions API method invocation issues and remote code execution (RCE) via template engine abuse. Can you explain that in simpler terms? what exactly are attackers doing?
Dr. Anya Sharma: essentially, attackers are exploiting weaknesses in how vBulletin handles internal requests and processes data within its template system. The first vulnerability, CVE-2025-48827, enables unauthorized access to specific functions within the vBulletin code. This is achieved by maliciously crafting URLs and triggering a specific flaw within the template engine involving the ‘replaceAdTemplate’ method. That method,when misused,allows attackers to inject code that bypasses security filters and directly execute commands on the server. We’re talking about remote code execution, where an attacker from anywhere in the world can control your server as if they were sitting right there. Critically, this is often unauthenticated remote code execution, meaning no username or password is required to carry out the attack against unpatched systems.
Time.news: The article points out that silent patches were likely released last year, but many forums remain unpatched. Why is this such a meaningful problem?
Dr. Anya Sharma: This is a classic and sadly, a very common problem in cybersecurity. Software vendors issue updates to address vulnerabilities, but it’s up to administrators to apply those updates. In the case of vBulletin, the patches (Patch Level 1 for version 6. and Patch level 3 for 5.7.5) likely went unnoticed by many, or were delayed due to other priorities.If a vulnerability has already been discovered and published,attackers know about it too by the time a patch is released. Unpatched forums are low-hanging fruit – easy targets for automated tools and malicious actors. This is why the timeframe between vulnerability disclosure and attack attempts are usually very short.
time.news: We’ve seen reports of exploitation in the wild originating from Poland. Should vBulletin administrators be concerned about widespread attacks?
Dr. Anya Sharma: Absolutely. The fact that these vulnerabilities are being actively exploited is a major red flag. The revelation of attack attempts by security researchers, combined with the availability of readily available exploit templates (like Nuclei templates), significantly lowers the barrier to entry for less sophisticated attackers.We can expect to see a considerable increase in exploitation attempts,even from less experienced attackers now that it’s very easy to execute the exploit. Unfortunately,forum owners who operate under the mindset of “It won’t happen to me” will typically be the biggest targets.
Time.news: vBulletin has a history of security issues. what makes it such a frequent target?
Dr. Anya Sharma: vBulletin’s widespread use as a commercial forum platform makes it an attractive target. Its modular design, while offering versatility and customization, inherently increases the attack surface – more code means more potential vulnerabilities. This is a trade off many modern software platforms experience. Also, I think notably vBulletin is often a self-managed and self-hosted platform, meaning the security is reliant on the forum owners and their staff, who typically aren’t trained as security professionals.
Time.news: What can vBulletin forum administrators do right now to protect their communities?
Dr. Anya Sharma: The absolute first thing to do is patch your vBulletin installation immediately. Upgrade to the latest version, 6.1.1 or later. That’s non-negotiable. Beyond that, I recommend implementing a Web Application Firewall (WAF) to filter out malicious traffic. Review your WAF configuration to make sure its rulesets incorporate protection from CVE-2025-48827 and CVE-2025-48828 exploits. Also, install and actively review your Intrusion Detection and Prevention Systems (IDS/IPS), monitor server logs for suspicious traffic, and implement multi-factor authentication, especially for administrator accounts. In complex environments it is always sensible to consider a third party to handle a security audit, especially if there is no in-house expertise available.
Time.news: The article mentions potential for ransomware attacks. How real is that threat?
Dr. Anya Sharma: The possibility is certainly real, though it hasn’t been widely observed yet*. Now that RCE has been demonstrated, attackers have full access to the server and associated data. The attacker will then simply encrypt the forum database as a next step and demand a ransom for its decryption. Thus, it’s a crucial consideration, to check your backup habitat is properly configured and segregated from the vBulletin Server. Also, implementing proper network segmentation will reduce the impact of a ransomware incident.
Time.news: Any final thoughts for our readers?
Dr.Anya Sharma: Don’t underestimate the importance of proactive security. Forum security is not a “set it and forget it” task. Regularly update your software, stay informed about emerging threats, and educate your users about security best practices. The security of your online community, and the privacy of your and your users’ data depends on it. Thanks for inviting me today.