The US Cybersecurity and Infrastructure Security Agency (CISA) has released a script to recover VMware ESXi servers encrypted by the recent widespread ESXiArgs ransomware attacks.
Starting last Friday, exposed VMware ESXi servers were the target of a widespread ESXiArgs ransomware attack.
Since then, the attacks have encrypted 2,800 servers according to a list of bitcoin addresses compiled by CISA technical adviser Jack Cable.
While many devices were encrypted, the campaign largely failed as the threat actors were unable to encrypt the flat files, where the data on the virtual disks is stored.
This vulnerability allowed Enes Sonmez and Ahmet Aykac from the YoreGroup technical team to devise a method to rebuild virtual machines from unencrypted flat files.
This method has helped many people to recover their servers, but the process has been difficult for some, and many people asked for help in our ESXiArgs support topic.
Launched script to automate recovery
To help users recover their servers CISA released a script ESXiArgs-Recover on GitHub to automate the recovery process.
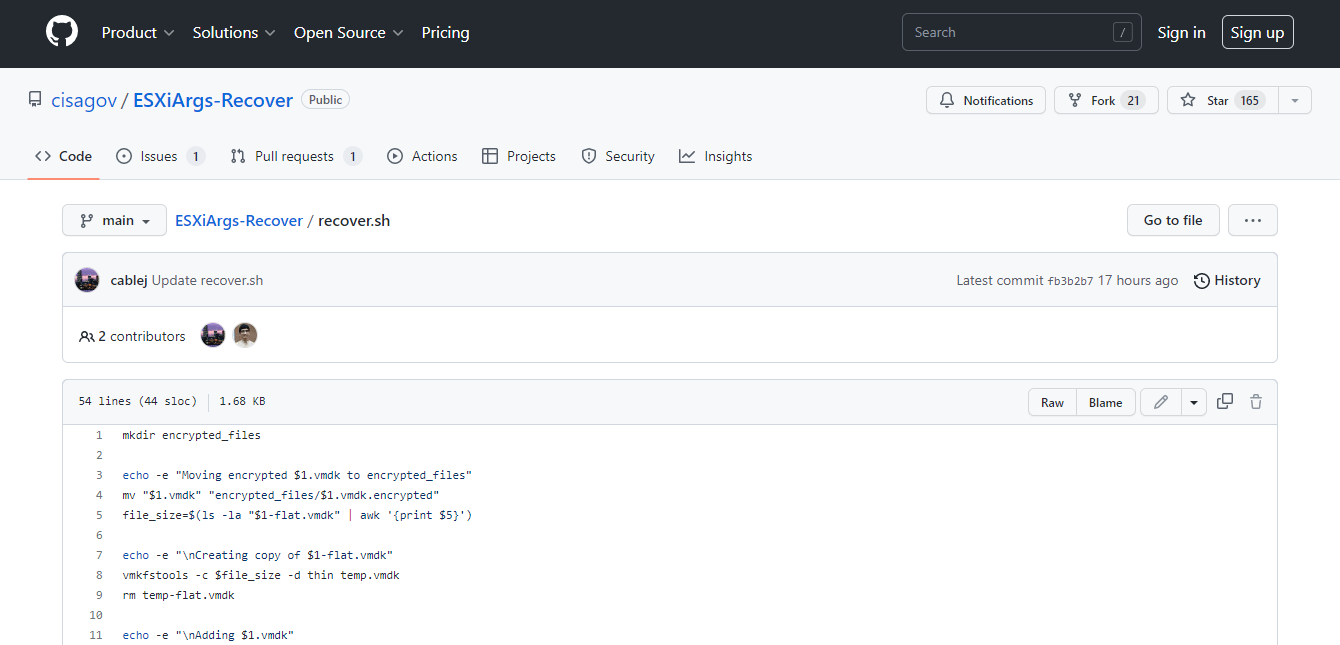
“CISA is aware that some organizations have reported success in recovering files without paying ransom. CISA compiled this tool based on publicly available resources, including a tutorial by Enes Sonmez and Ahmet Aykac,” explains CISA.
“This tool works by rebuilding virtual machine metadata from virtual disks that were not encrypted by the malware.”
While the GitHub project page has the steps you need to recover virtual machines, in summary the script will clean up a virtual machine’s encrypted files and then attempt to rebuild the virtual machine’s .vmdk file using the unencrypted flat file.
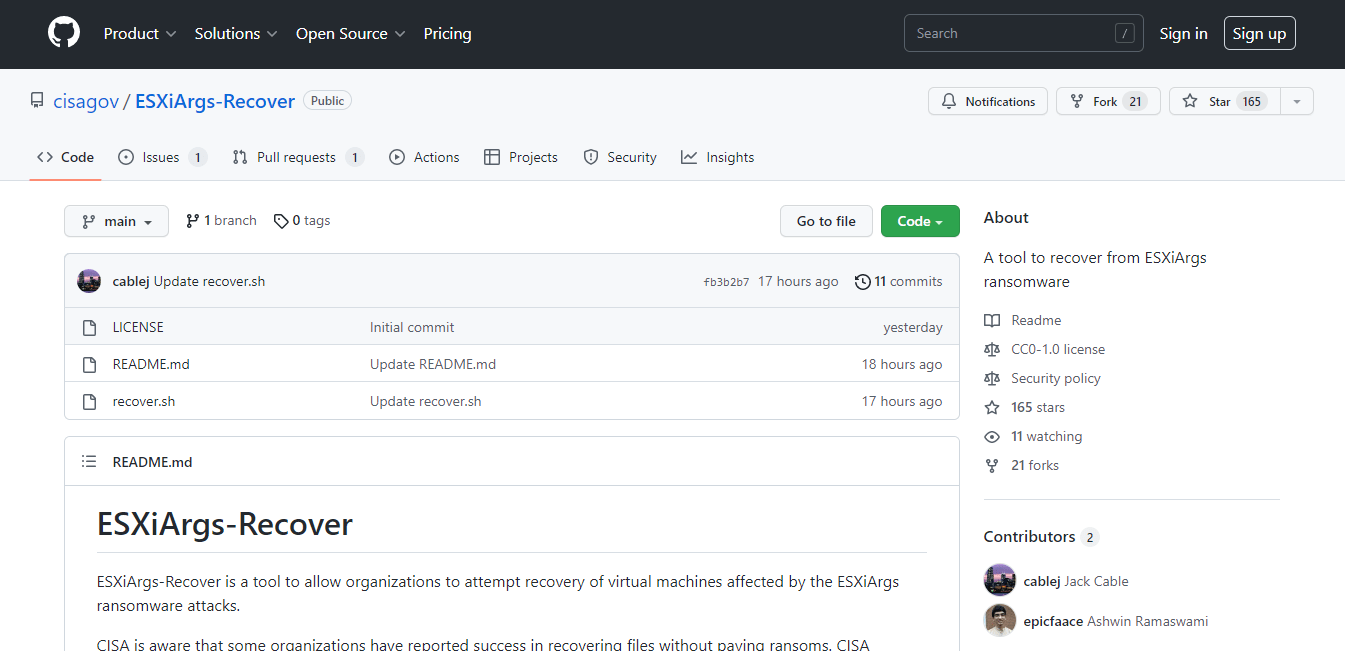
When done if successful you can register the virtual machine again in VMware ESXi to get access to the VM again.
CISA encourages administrators to review the script before using it to understand how it works and avoid potential complications. While the script shouldn’t cause any problems, researchers strongly recommend that backups be created before attempting recovery.
“While CISA works to ensure that scripts like this are safe and effective, this script is provided without warranty, either express or implied.” warns CISA.
“Do not use this script without understanding how it may affect your system. CISA assumes no responsibility for any damage caused by this script.”
Fuente: https://www.bleepingcomputer.com/news/security/cisa-releases-recovery-script-for-esxiargs-ransomware-victims/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He has also worked for security companies such as Kaspersky Lab. His daily work includes investigating new malware and cybersecurity incidents. He also has a deep level of knowledge in mobile security and mobile vulnerabilities.
Send news tips to [email protected] or www.instagram.com/iicsorg/
You can also find us on Telegram www.t.me/noticiasciberseguridad
