2023-05-12 00:57:49
On Tuesday, Microsoft issued an updated patch to address a vulnerability that had been previously fixed in March, but was later found to be ineffective by researchers in the security community.
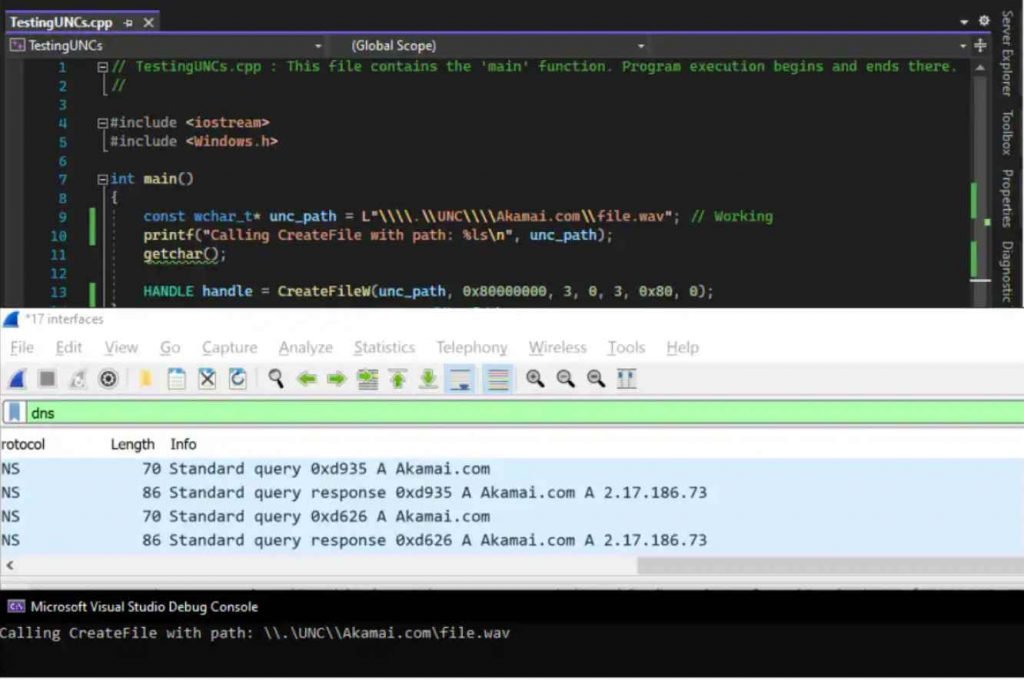
Ben Barnea, a researcher at Akamai, found a method around the flaw that had been fixed in March. In this way, an attacker could exploit the vulnerability to force an Outlook client to connect to a server that was controlled by the attacker. Although the issue was fixed in March, the researcher found a way around the patch.
Barnea said the issue is a zero-click vulnerability, which means it can be triggered without user interaction, and all versions of Windows are vulnerable to it. Barnea elaborated by saying that the original patch was pointless for the introduction of only one new character. However, he and Akamai’s security team disagreed with how Microsoft categorized the issue, which was assigned a CVSS score of just 6.5. They found it when they were looking at the patch for CVE-2023-23397, which fixed the problem by changing the code flow in Outlook so that it now checks if the Universal Naming Convention (UNC) path that retrieves the custom sound file references to an Internet URL, and if it does, it uses the default reminder sound instead of the custom one.
Unfortunately, they also discovered that the check (and consequently the patch) can be easily broken by adding a single character, which would alter the way a certain function categorizes the UNC path zone. This was a disappointing find.
Also, according to a recent study carried out by Cybernews, more than 85,000 Microsoft Exchange servers do not have the necessary patches installed to protect them from multiple vulnerabilities that allow remote code execution and were resolved by Microsoft in February 2023.
Threat actors can remotely execute code on the target computer thanks to the vulnerabilities in question, which are logged as CVE-2023-21529, CVE-2023-21706, and CVE-2023-21707. These vulnerabilities are tracked as CVE-2023-21529, CVE-2023-21706, and CVE-2023-21707.
Although there have been no reports of attacks exploiting these issues at the time, Microsoft recommended companies update their servers as quickly as possible. This is because, in theory, hackers could have exploited the holes to gain initial access to a corporate network. However, there have been no reports of attacks using these issues.
However, research findings indicated that more than three months after security updates became available, many businesses that use Microsoft Exchange software are still susceptible to security flaws.
The team found that one in three Microsoft Exchange servers were still missing the patch, most of which are located in Germany (nearly 18,000 of them).
The researchers examined a total of 248,350 Internet-connected Microsoft Exchange servers. They found that 85,261 of those servers, or 34.33%, were vulnerable to RCE attacks.
The United States of America is the second most affected nation in the world, with approximately 16,000 servers still to be patched. They are followed by the United Kingdom (3,734), France (2,959), the Netherlands (2,906) and Russia (2,775).
In addition, the researchers evaluated the distribution of Exchange versions and found that, in most Western countries, newer versions that were still susceptible were more frequent, with the exception of the first minor version in a major version (for example, version 15.2.986.5 instead of 15.2.986.41).
The researchers found that older versions of Microsoft Exchange 2016 were preferred in the China and Russia cases, even though newer versions were being used in the 2019 and 2013 releases. This was the case even though there were older versions. new available.
Despite the fact that many months have passed since the RCE issues were discovered, the number of Exchange servers still missing their patches is only slightly decreasing. The researchers noted that the number of susceptible servers in February was around 87,000, as shown by statistics provided by the Shadowserver Foundation.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He has also worked for security companies such as Kaspersky Lab. His daily work includes investigating new malware and cybersecurity incidents. He also has a deep level of knowledge in mobile security and mobile vulnerabilities.
Send news tips to [email protected] or www.instagram.com/iicsorg/
You can also find us on Telegram www.t.me/noticiasciberseguridad
#Hack #Outlook #email #accounts #.wav #music #file
