2024-07-23 22:29:10
In a major cyber security revelation, a zero-day vulnerability has been discovered in the Telegram messaging app for Android, called ‘EvilVideo’, which allows attackers to send malicious Android APK uploads disguised as video files. This exploit, which has been spotted recently, was a serious threat to millions of Telegram users around the world.
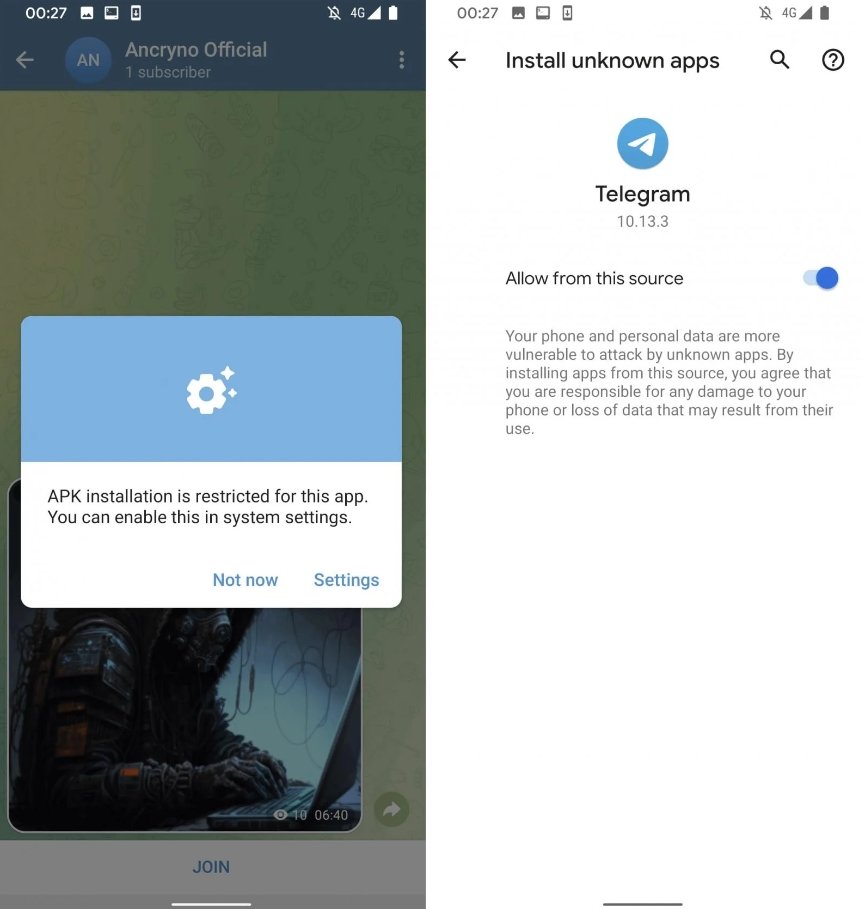
The vulnerability was discovered by cybersecurity researchers who found that threat actors could create malicious APK files that appeared as video files within the Telegram app. When users tried to play these videos, they were prompted to open the file in an external application, which resulted in the malicious APK being installed and potentially damaging the user’s device.
Telegram’s zero-day ‘EvilVideo’ vulnerability allowed attackers to send Android APK files disguised as video files. This exploit was mainly due to insufficient file validation and improper handling of media files within the Telegram Android app.
Cultivation process:
- Preparation of the malicious APK:
- File header modification: The attackers created a malicious APK file by modifying its header and metadata to mimic a legitimate video file. This involves changing the file extension and adjusting the header information so that the APK file appears as a common video format such as MP4 or AVI.
- Embedding malicious code: The APK file was embedded with malicious payloads, which could range from spyware to ransomware. This payload was designed to perform specific actions when installed on the victim’s device.
- Disguise the malicious payload:
- File metadata manipulation: The attackers manipulated the file’s metadata to ensure that the file was not suspicious in Telegram’s initial inspection. This included changing the MIME type and file extension for those associated with video files.
- Creating an attractive appearance: The file was named and presented in a way that would not immediately arouse suspicion in the user. For example, it could be called “vacation_video.mp4” to appear as an innocent video.
- Malicious delivery of APK via Telegram:
- Sending the file: The attacker sent the disguised APK file to the target via Telegram. Due to a Telegram file handling vulnerability the application was able to accept the file and present it as a video.
- Initial user interaction: The recipient sees the file as a video and tries to play it on Telegram. The app, recognizing the file as a video, tries to play it but fails due to its true APK nature.
- To activate the interest:
- Error notice: When the user tries to play the “video”, Telegram displays an error message saying that the video cannot be played within the application. It then prompts the user to open the file using an external application.
- Run the malicious APK: If the user agrees to open the file externally, the file handler of the operating system processes the file as an APK and executes it. This results in the installation of the malicious payload on the device.
- Post-processing Actions:
- Pay application: Once installed, the malicious APK can perform various malicious activities depending on the attacker’s intent. This may include exfiltrating personal data, encrypting files for ransom, or creating backdoors for further exploitation.
- Durability maintenance: Malware can also establish persistence on the device, ensuring that it remains active even after rebooting or attempting to remove it.
Technical details of the benefit:
- Forging metadata and file headers: By changing the file header and metadata, attackers could bypass Telegram’s surface file validation checks.
- MIME type manipulation: By changing the MIME type to video formats such as “video/mp4” Telegram was prompted to treat the APK file as a video.
- Error handling exploit: Leveraging the error prompt mechanism, the attackers directed users to run the APK file using external applications, where the Android OS would reveal and execute the true nature of the file.
Mitigation and Prevention:
- Improved file validation: The Telegram patch involved implementing stricter file validation processes, ensuring that files were thoroughly verified before being accepted as media files.
- User Education: Educating users about the risks of opening unknown files and the importance of verifying the source of received media can reduce the likelihood of such exploits being successful.
- Security software: Using robust security apps that can detect and block malicious APKs, even when they’re disguised as media files, adds an extra layer of protection.
Best practices for users:
- Keep apps up to date:
- Always ensure that applications, especially those that handle sensitive information or media, are updated to the latest versions to take advantage of security patches and improvements.
- Be careful with unknown files:
- Avoid opening files from unknown or untrusted sources. Be especially careful with media files that ask external applications to run.
- Employing security solutions:
- Use robust security software to detect and mitigate potential threats. This includes antivirus programs and malware scanners that can identify and block malicious APKs.

He is a recognized expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cybersecurity analyst in 2003. He works actively as an anti-malware expert. He also worked for security companies like Kaspersky Lab. He also has a deep level of knowledge of mobile security and mobile vulnerabilities.
Send news tips to [email protected] or www.instagram.com/iicsorg/
You can also find us on Telegram www.t.me/noticiasciberseguro
#hack #phone #Telegram #Video

