One day, in October 2021, the Hillel Yaffe hospital staff discovered that access to its information systems was blocked. This was not a technical glitch, but a hack by ransom demanders. The hospital did not pay the ransom, but the attack caused damage that was retrospectively estimated at approximately NIS 36 million.
The attack required the hospital to quickly set up alternative computer systems, and until this is done, manual registration of the medical information is required (fortunately, there are still people in the system who remember how to do this). Although the vital systems of the hospital were not damaged, some surgeries and treatments were postponed until the strength of the blow became clear. It took the hospital about a month to return to full computerized activity, and several more months to regain the full capabilities that were lost. This is considered a quick recovery after such an event, but it is still a trauma for the hospital, and a defining event in the entire healthcare system.
“Everyone who is involved in medical cyber in Israel today says that they were involved in the recovery from the Hillel Yaffe incident,” says Shashu, an information systems manager at another hospital, with a doubt. “It’s like you said about your weapon: battle-tested in the Israeli-Palestinian conflict.”
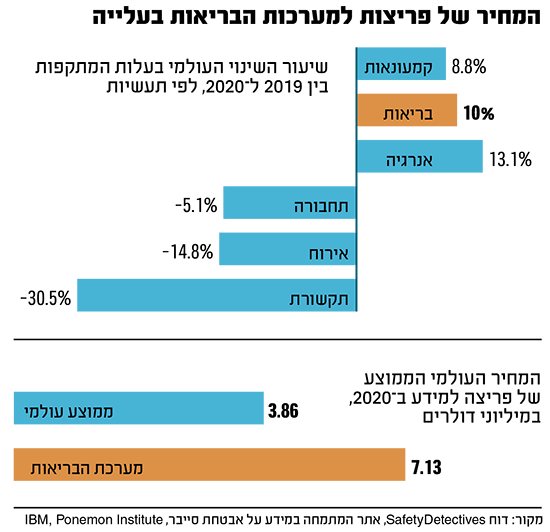
This event has received a lot of attention, but it is only the tip of the iceberg. In recent years, health systems in France, Germany, Great Britain and Ireland have experienced a series of large attacks that have disrupted the operations of their hospitals. In Israel, there are hundreds of thousands of attacks on the health system per month. Meanwhile, there has not yet been an attack that caused so much damage as in Hillel Yaffe, although in July 2021 the website activity of several hospitals was disrupted.
“There were other attacks on the health system, albeit on a smaller scale, that did not reach the media,” says an official in the health system. “Every hospital doesn’t want to advertise that it has been attacked, with the notion that if I am attacked enough, eventually something will work. It is customary not to talk about the attacks, so as not to broadcast that we are vulnerable. It attracts fire.”
This week we received a reminder of the vulnerability of systems of this type, when hackers demanded a ransom for the release of personal information taken from the Technion’s computers. Although it is not a medical organization, the guiding principles of such an attack are similar.
Hundreds of dollars for a medical record
The attackers of health systems are divided into three main types, says Gal Gnainsky, head of the security group of the global Philips Corporation. One type are attackers who work in coordination with their state institutions, for the purposes of terrorism or stealing technological secrets. “They can enter the systems through our partners in that country, or through the academy, with which we work. In some cultures, this is considered patriotic. We are in contact with the governments and exert our pressure so that these moves are stopped. We must manage this risk, understanding that some of our secrets They will leak, but we are technologically renewed all the time, so the harm from stealing the secrets is up to a certain limit.”
One of the biggest concerns is the building of a bank of targets for medical officials who will be attacked during a conflict. “The Iranians, let’s say, have an interest in sitting inside the servers for years, and on the day of an order to attack the medical equipment,” says Ran Harel, director of the product department at the cyber company Semperis Israel.
The more common type of attack is economic. “The hackers behave like a high-tech company in every way,” says Amos Benzur, partner and head of the pharma, health systems and regulation practice at the Shabulat & Co. law firm. “They come to decorated offices in the morning and try to convey credibility and fairness, because this is what gives the attacked company the confidence that if it pays the ransom, the information will really be returned to it.” The hackers, he says, are usually “kids who want money”, but behind the companies are criminal organizations.
“It’s easier for them to ask for a ransom than to steal and sell the information,” adds Harel, “because that way they don’t have to find someone to sell it to.” But selling medical information is also an attractive business: several hundred dollars per record.
Ran Harel / Photo: SEMPERIS
A third group of hackers are activists and disgruntled people in organizations. These are rarer attacks, but can be more deadly. The answer to them is to choose the employees well, and compartmentalize privileges.
What happens when there is an attack? Is it allowed to pay the ransom?
Gnainsky: “In the past, organizations tended to pay the ransom immediately. Today they pay less, and the regulator recommends not paying, but as far as I understand it is not prohibited either. The one who pays is usually the one who does not have backup or a good recovery plan, so payment may damage the institution’s reputation.”
Benzur: “This is an interesting and unclear issue. It is forbidden to pay terrorist organizations, and not to take part in money laundering.”
The security problem of the startups
To date, there has not been an attack on medical equipment inside a patient’s body, but there have been hacks to prove such a capability, and it does exist. The responsibility for the protection of medical devices is shared between the manufacturers and the hospitals that use it.
In Israel, it is not necessary to prove a device’s resistance to cyber attacks in order to market it, but the hospital is obligated to purchase medical devices according to the cyber safety guidelines of the Ministry of Health. The State Comptroller’s report on cyber safety in the health care system published in 2022 recommended that approval of medical devices for marketing in Israel also require compliance with cyber safety standards.
In the US, there are already several procedures that must be followed, such as the creation of a “software bill of materials”, which defines where each software component for the product is purchased. According to Selva Bronfman, CEO of Saiblom from the LG Group, which operates in the field of cyber risk assessment In devices, the FDA does not talk about specific safety components but about processes. “Do you have recovery processes from shutdown? Is there separation between the device and the information stored in it? Do you have regular monitoring processes for the device?”.
The changes in the field are fast, and developers of medical devices that start today will probably meet stricter regulation when they reach the market. But for young companies with few employees, it is difficult to allocate resources to the cyber field. “The medical device companies are not sufficiently aware of the matter, because they are not the ones being attacked,” Benzur says.
“When we examine start-ups for purchase, or work with them as suppliers, we always see incredible deficiencies in this area,” says Gnainsky. “This is to be expected, but it is a problem. There were purchase deals that were canceled for this reason. Another possibility is that we will invest the necessary capital to bring the start-up to a proper state, but this may come at the expense of the amount that the start-up will receive in the deal.”
Dirk de Wit, head of product security at Philips, adds: “The startup people are not always used to all this bureaucracy and sometimes it can even make them leave.”
In a survey conducted by cyber security company Saiblom, 75% of medical device companies, both large and small, did not have a senior management member responsible for cyber security. Only 46% of respondents said that they manage to comply with all the security regulations of the US Food and Drug Administration. 99% of companies increased their device security budget this year, yet 79% say speed to market is more important than security. 39% said that today they react to security threats and are not proactive enough in defense.
What should be done immediately when establishing the company?
Gnainsky: “Appoint one person that is his job, and he has specific experience in protecting medical equipment, or at least equipment, not just networks.”
Bronfman: “It is possible relatively cheaply to implement documentation processes, such as keeping the list of software components, to put security processes in place. You don’t need to show that the device is unhackable, but you have the process to protect it. If you didn’t build the process together with the device, it is much more difficult to do that Later”.
What do you think other medical device companies should also do?
De Wit: “We employ ‘good’ hackers who look for our weak points, and also cooperate with parties who do these tests independently, in order to create a reputation for themselves as hackers. When we know that there was an attack on our device, we inform all the hospitals that work in front of us”.
The hospitals do not allocate enough budgets
On the other side of the equation are the hospitals, which are considered the first responsible party for protection against harm. “The division of responsibility between the hospitals and the device companies is not always legally clear,” says Shani Matan, a privacy protection expert in the pharma and health systems practice at Sheblat Co.
It can be said that the device companies are responsible for actively looking for possible loopholes for the devices and providing software updates. “Today they do this less frequently than companies in sectors such as banking or automobiles,” says Bronfman. The hospitals are responsible for installing the software updates on time, which is not always easy to do. For this, the hospital’s work routine has to be interrupted and sometimes essential devices have to be disabled. However, when you don’t, the price can be high. The attack in Hillel Yaffe could have been prevented through a software update.
Another unique challenge for health systems is the connection between many different systems, some new and some old. A CT device purchased for millions of dollars will not be replaced just because it runs on an old operating system. Some of the equipment was not designed to connect to the computer network at all, and the connection was made retrospectively.

The challenges come against the background of a low budget and low managerial attention to the issue. The challenges come against the background of a low budget and low managerial attention to the issue, and the education of the employees in hospitals is a critical process. “If I don’t get to the point where the nurse finds it strange that a patient sat in her chair in front of the computer, then I won’t be able to stop him,” says an official in the health system.
The State Comptroller’s report for 2022 stated that hospitals are not sufficiently prepared for cyber attacks. Out of 11 medical centers examined, 6 did not allocate to cyber defense the budget established by a government decision – 8% of the information security budget.
“Bulking up to hundreds of attacks a month”
The report also indicated that from 2018 the cyber protection procedures were not updated by the Ministry of Health. The procedures are being updated these days.
Since 2016, the Ministry of Health has had a cyber unit subordinate to the national cyber system, whose role is not only to formulate procedures but to actually help the hospitals. The Ministry of Health purchased a system for risk mapping and protection for all health organizations.
In addition, a national project was established that centralizes all monitoring in one center. At first it was voluntary and today everyone is monitored 24/7. The cyber center detects attacks in the world and alerts the hospitals. He purchases and manufactures blocking tools himself.
“The Ministry of Health is making efforts to be a regulator that doesn’t bother but helps,” praises a source in the market, “and the fact that they are pouring in resources is a miracle. But as far as we are concerned, their systems still do not provide the full answer.”
