2024-06-10 18:31:53
Sustainable Analysis has found a big safety vulnerability affecting Azure clients who depend on service tags for his or her firewall guidelines. This vulnerability permits attackers to bypass Azure firewall guidelines, which poses a big threat to organizations utilizing these configurations. Under is an in depth have a look at the vulnerability, how it may be exploited, and key defensive measures to mitigate the danger.
GET STARTED IN AZURE APPLICATION INSIGHTS
Sustainable Analysis he came upon first the vulnerability inside Azure Software Insights, a service designed to watch and analyze the efficiency and availability of internet functions. The Availability Check characteristic of Azure Software Insights, meant for testing the accessibility and efficiency of functions, was discovered to be prone to abuse. Customers can management server-side requests in these assessments, together with including customized headers and altering HTTP strategies. Attackers can exploit this management to forge requests to trusted providers, mimicking a server-side request forgery (SSRF) assault.
EXPAND TO MORE THAN 10 OTHER AZURE SERVICES
After additional investigation, Tenable Analysis discovered that the vulnerability extends past Azure Software Insights to greater than 10 different Azure providers. These embrace:
- Azure DevOps
- Azure Machine Studying
- Azure logic functions
- Azure Container Registry
- Azure load take a look at
- Azure API Administration
- Azure Knowledge Manufacturing facility
- Azure Motion Group
- Azure AI Video Indexer
- Blue chaos studio
Every of those providers allows customers to regulate server-side requests and has an related service tag, which poses potential safety dangers if not correctly mitigated.
HOW CAN A LOAN SHOW VULNERABILITY
Attackers can exploit the vulnerability in Azure service tags by abusing the Availability Testing characteristic in Azure Software Insights. Under are steps and examples to exhibit how an attacker can exploit this vulnerability:
1. Availability take a look at setup:
- Instance case: An attacker identifies an inside internet service inside the Azure surroundings of a sufferer that’s protected by a firewall rule that permits site visitors solely from Azure Software Insights.
- Motion: The attacker units up an availability take a look at in Azure Software Insights and configures it to level to the interior internet service.
2. Customise the Software:
- Header manipulation: The attacker customizes HTTP request headers to incorporate authorization tokens or different headers that the goal service would possibly count on.
- Change HTTP strategies: The attacker can change the HTTP technique (for instance, from GET to POST) to carry out actions corresponding to sending knowledge or invoking actions on the goal service.
- Personalization instance: The attacker configures the take a look at to ship a POST request with a customized “Authorization: Bearer” header.
3. Sending the malicious request:
- Firewall Bypass: The design utility is submitted by way of the provision take a look at. As a result of it comes from a trusted Azure service (App Insights), it bypasses firewall guidelines based mostly on service tags.
- Instance Assault: The provision take a look at sends the POST request with the customized header to the interior internet service, which processes the request as if it have been from a official supply.
4. Entry to inside assets:
- Unauthorized entry: The attacker now has entry to inside APIs, databases, or different providers that have been protected by the firewall.
- Out-filtering and dealing with: The attacker can exfiltrate delicate knowledge, manipulate inside assets, or use the entry to launch additional assaults.
- Instance of impression: The attacker retrieves delicate knowledge from an inside API or modifies configuration settings in an inside service.
EXAMPLE DETAILED EXPLOITATION
View: A company makes use of Azure Software Insights to watch an inside monetary service. The service is protected by a firewall rule that solely permits entry from the ApplicationInsightsAvailability service tag.
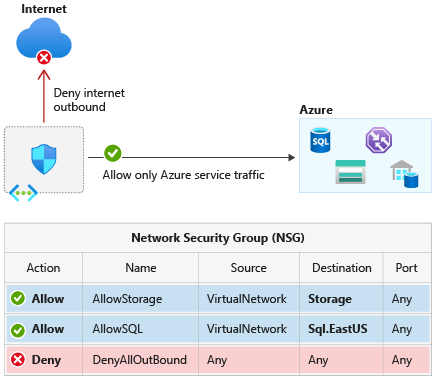
- Inside Azure utility service deployment:
- Your group has a monetary utility hosted on an Azure utility service and firewall guidelines are configured to just accept solely site visitors from the ApplicationInsightsAvailability service tag.
- Entry try by the attacker:
- The attacker discovers the interior monetary utility endpoint and tries to realize direct entry to it. The firewall blocks this try and returns a forbidden response.
- Exploit the vulnerability:
- Check setup: The attacker units up an availability take a look at in Azure Software Insights that targets the interior monetary utility.
- Request for personalization: The attacker customizes the take a look at to ship a POST request with a payload that triggers a monetary transaction, including a customized “Authorization: Service” header.
- Sending the request: the provision take a look at sends the POST request to the interior monetary utility, bypassing the firewall.
- Get unauthorized entry:
- The monetary utility processes the POST request, believing it to be from a official supply. The attacker efficiently initiates the monetary transaction.
- Out-filtering: The attacker configures one other availability take a look at to ship GET requests with customized headers to extract monetary data from the appliance.
Superior Cultivation Methods
1. Chain assaults:
- Attackers can chain a number of vulnerabilities or providers to extend their privileges and affect. For instance, use the preliminary entry gained within the availability take a look at to entry different inside providers or to raise privileges inside the Azure surroundings.
2. Lateral motion:
- As soon as contained in the community, attackers can transfer laterally to compromise different providers or extract extra knowledge. They will use different Azure providers, corresponding to Azure DevOps or Azure Logic Apps, to seek out further entry factors or delicate knowledge.
3. Everlasting entry:
- Attackers can configure long-term availability assessments to run periodically, making certain steady entry to inside providers. They might use these persistent probes to keep up a base inside the surroundings, repeatedly extract knowledge or carry out malicious actions.
PROTECTIVE MEASURES
To mitigate the dangers related to this vulnerability, Azure clients ought to implement a number of protecting measures:
1. Analyze and replace community guidelines:
- Totally evaluation community safety guidelines.
- Establish and analyze any use of service tags in firewall guidelines.
- Assume that providers protected by service tags alone could also be weak.
2. Implement sturdy authentication and authorization:
- Add sturdy authentication and authorization mechanisms.
- Use Azure Energetic Listing (Azure AD) to handle entry.
- Implement multi-factor authentication and the ideas of least privilege.
3. Enhance community isolation:
- Use community safety teams (NSG) and utility safety teams (ASG) for granular isolation.
- Deploy Azure Non-public Connection to maintain site visitors inside the Azure community.
4. Monitor and audit community site visitors:
- Allow logging and monitoring of community site visitors.
- Use Azure Monitor and Azure Safety Middle to configure alerts for uncommon actions.
- Periodically evaluation logs and audit trails.
5. Patch and periodic replace providers:
- Maintain all Azure providers and functions updated with safety patches.
- Monitor safety advisories from Microsoft and different sources.
- Apply updates shortly to attenuate threat.
6. Use Azure Coverage to use safety settings:
- Deploy Azure Coverage to implement safety greatest practices.
- Create insurance policies that require sturdy authentication and correct community configurations.
- Use Azure Coverage Initiatives for constant enforcement throughout assets.
7. Conduct safety assessments and penetration assessments:
- Conduct common safety assessments and penetration assessments.
- Contact safety consultants or third-party providers for a radical evaluation.
- Use instruments like Azure Safety Benchmark and Azure Defender.
8. Training and coaching of workers:
- Present coaching on dangers and greatest practices associated to Azure service tags and community safety.
- Guarantee workers perceive the significance of multi-layered safety.
- Equip groups to successfully implement and handle safety measures.
The vulnerability found by Tenable Analysis highlights the numerous dangers of relying solely on Azure service tags for firewall guidelines. By understanding the character of the vulnerability and implementing beneficial safety measures, Azure clients can higher shield their environments and mitigate potential threats. Common critiques, updates, and a multi-layered safety method are important to sustaining a safe Azure surroundings.

Cyber safety fanatic. Data safety specialist, at present working as a threat infrastructure specialist and researcher.
Expertise in threat and management processes, safety audit help, COB (enterprise continuity) design and help, work group administration and knowledge safety requirements.
Ship information tricks to [email protected] or www.instagram.com/iicsorg/.
You can even discover us on Telegram www.t.me/noticiasciberseguro
#Azure #safety #threat #hackers #exploit #Azure #service #tags #cease

