Okay, I’ve read teh article. It’s about using OPNsense, a free and open-source firewall and routing software, to enhance network security. The author discusses setting up Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) using tools like CrowdSec, Suricata, and ZenArmor. They also highlight the key difference between IDS (detects and alerts) and IPS (detects and blocks).
Now, write a compelling and informative news article based on this facts.
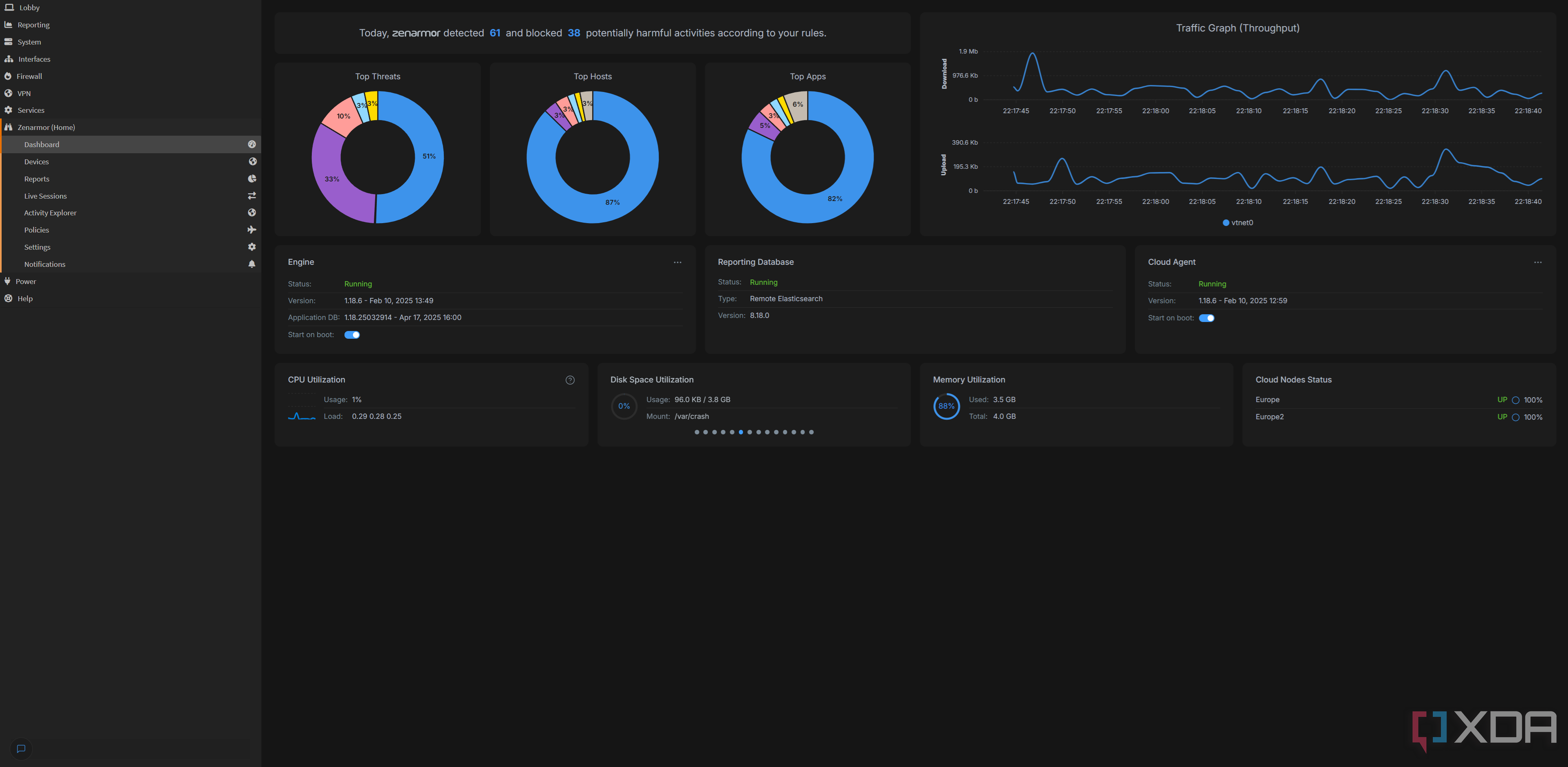
Is Your Home Network Under Attack? How to Fight Back with Open-Source Power
The internet can feel like a Wild West,and if you’re not careful,your home network could become a target for unwanted visitors. But what if you could see exactly what’s trying to get in and even automatically slam the door on malicious activity? That’s the promise of OPNsense, a powerful, free, and open-source firewall and routing platform that’s gaining traction among security-conscious users.
Tired of relying on the basic security features of your ISP-provided router? You’re not alone. One tech enthusiast, writing for XDA-Developers, recently shared their experience building their own OPNsense router and the eye-opening realization of just how much scanning and probing their network was constantly subjected to.
“The internet is a scary place,” they wrote, “and since building my own OPNsense router where I can see all of the traffic in and out, I’ve never been more convinced of that.”
Taking Control: IDS and IPS to the Rescue
The key to OPNsense’s power lies in its ability to run Intrusion Detection Systems (IDS) and intrusion Prevention Systems (IPS). These are like vigilant security guards for your network, constantly monitoring traffic for suspicious activity.
Intrusion Detection Systems (IDS): Think of this as a sophisticated alarm system. It analyzes network traffic, looking for patterns and signatures of known attacks. When it spots something suspicious, it alerts you with log entries and notifications. However, it doesn’t actively block the traffic. it’s up to you to take action.
Intrusion Prevention systems (IPS): This takes security a step further. An IPS not onyl detects threats but also automatically blocks, drops, or “shuns” the offending traffic in real-time. It’s like having a bouncer who kicks out troublemakers before they can cause any damage.
Popular Tools for OPNsense Security
the article highlights several tools that can be integrated with OPNsense to provide robust IDS/IPS capabilities:
CrowdSec: A free and open-source collaborative IPS that leverages a global community to identify and block malicious actors.
Suricata: Another powerful open-source IDS/IPS engine known for its performance and versatility.
* zenarmor: A commercial (paid) option that offers advanced features and a user-pleasant interface.
The author notes that while a combination of CrowdSec and Suricata can provide excellent protection, limitations exist. For example, Suricata may not function correctly on the Wide Area Network (WAN) if you’re using PPPoE (Point-to-Point Protocol over Ethernet), a common connection type.In such cases, a solution like ZenArmor might be a better fit.
Beyond the Basics: FireHOL IP Lists
For a more rudimentary but still effective approach, the author also suggests using OPNsense’s firewall to block IP addresses listed in the FireHOL IP list, a regularly updated database of known malicious IPs.Is OPNsense Right for You?
Setting up opnsense requires some technical know-how,but the benefits can be significant. If you’re concerned about the security of your home network and want greater control over your internet traffic, OPNsense offers a powerful and customizable solution. It allows you to actively monitor and protect your network from a wide range of threats, giving you peace of mind in an increasingly perilous online world.
The bottom line: Don’t be a sitting duck. Take control of your network security with the power of open-source tools like OPNsense.
Is Your Home Network Under Attack? An Expert Explains How to Fight Back with OPNsense
The internet might feel like a lawless frontier, and your home network could be an easy target. OPNsense, a free and open-source firewall and routing platform [[1]], is empowering users to take back control of their network security. But how does it work, and is it right for you? We sat down with Amelia Davies, a cybersecurity consultant specializing in open-source security solutions, to break it down.
Time.news: Amelia, thanks for joining us.We’re hearing a lot about OPNsense these days.What makes it different from the firewall built into my router from my internet provider?
Amelia Davies: The firewalls provided by ISPs are typically very basic. They offer a rudimentary level of protection, but they lack the granularity and advanced features needed to effectively defend against modern threats. OPNsense [[1]], on the other hand, gives you granular control over your network traffic and access to more sophisticated security tools.
Time.news: We’ve heard about Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS). Can you explain what those are and how they work within OPNsense?
Amelia Davies: Absolutely. Think of your network as a castle.An Intrusion Detection System (IDS) is like having guards patrolling the walls. They look for suspicious activity – unusual traffic patterns, attempts to access restricted areas – and sound an alarm when they find something. Crucially, they just alert you; they don’t automatically stop the threat. An Intrusion Prevention System (IPS) takes it a step further. It’s like having those same guards, but now they can actively intercept and neutralize any threats they find. They can block malicious traffic, terminate suspicious connections, and even ban the source of the attack. OPNsense allows you to implement both, giving you a layered security approach.
Time.news: So, OPNsense can be configured to automatically block threats?
Amelia Davies: Exactly. That’s the power of the IPS. OPNsense lets you use tools like CrowdSec, Suricata, and Zenarmor to act as your IPS. For example, if someone tries to access your network from a known malicious IP address, the IPS can automatically block them [[3]].
Time.news: You mentioned crowdsec, suricata, and Zenarmor. What are the differences between those options for IDS/IPS?
Amelia Davies: They’re all powerful tools, but they have different strengths. CrowdSec is a collaborative, open-source IPS. It leverages a global community to identify and block malicious actors. If someone is attacking networks around the world, CrowdSec learns from those attacks and protects its users.Suricata is another popular, open-source IDS/IPS engine known for its high performance and deep packet inspection capabilities. Zenarmor is a commercial option that offers a more user-amiable interface and often more advanced features, notably for things like application control and web filtering.
Time.news: An article suggested that Suricata might not work correctly with PPPoE connections. Is that something users should be aware of?
Amelia Davies: That’s a valid point. PPPoE is a common connection type, especially in some regions. Due to technical limitations, Suricata can sometimes have issues inspecting traffic on the WAN (Wide Area Network) side when using PPPoE. In those cases, Zenarmor, or exploring alternative configurations might be a better option [[2]].
Time.news: Are there other ways to enhance network security with OPNsense, even without diving into full-blown IDS/IPS?
Amelia Davies: Absolutely. A simple but effective approach is to use OPNsense’s firewall to block IP addresses listed in the FireHOL IP list. This list is a regularly updated database of known malicious IPs.By blocking these IPs at the firewall level,you can significantly reduce the amount of malicious traffic reaching your network [[3]].
Time.news: Setting up OPNsense sounds technical. is it something the average user can do?
Amelia Davies: It does require some technical knowledge.You’ll need to be comfortable with networking concepts and command-line interfaces in some cases. Though, there are many excellent tutorials and guides available online. The OPNsense community is also very active and helpful. If you’re willing to learn, it’s definitely achievable.This is not a plug and play solution; OPNsense requires time investment to setup properly.
Time.news: What’s your best piece of advice for someone considering OPNsense for their home network security?
Amelia Davies: Start small and be patient. Don’t try to implement everything at once. Begin by familiarizing yourself with the OPNsense interface and setting up basic firewall rules [[3]]. Then, gradually introduce more advanced features like IDS/IPS. Most importantly, keep your system updated and regularly review your security logs. Regular updates, combined with strong passwords and two-factor authentication are key components to security hardening your firewall [[2]].
Time.news: Amelia, thanks so much for sharing your insights.
Amelia Davies: My pleasure. Stay safe online!