2023-05-17 16:16:00
Check Point Research has been monitoring sophisticated attacks against authorities in numerous European countries since January 2023. The campaign made use of a large number of tools, one of which was an implant, which is a tactic often linked to cybercriminals. backed by the Chinese government. This action has substantial infrastructural similarities to previously published activities by Avast and ESET, linking it to the “Mustang Panda” malware family. This group of suspicious behavior is being monitored by CPR as “Camaro Dragon” at this time.
According to Check Point experts Itay Cohen and Radoslaw Madej, an investigation into these attacks has uncovered a custom firmware implant that was created specifically for TP-Link routers. “The implant features several malicious components, including a custom backdoor called ‘Horse Shell,’ which allows attackers to maintain persistent access, build anonymous infrastructure, and allow lateral movement into compromised networks,” the firm stated.
“Due to the firmware agnostic design of the implant,” its components can be incorporated into different types of software by a variety of different manufacturers. At this time, the precise mechanism that was used to distribute the tampered firmware images to the compromised routers is unclear. Likewise, its use and participation in real attacks is also unknown. It is believed that the first access could have been gained by exploiting known security holes or by brute force devices that had passwords that were either default or easy to guess. Based on what is currently known, the C++-based Horse Shell implant gives attackers the ability to execute arbitrary shell commands, upload and download files to and from the router, and relay communication between two separate clients. However, in an intriguing turn of events, the router backdoor is suspected of targeting random devices on residential and home networks. This finding lends credence to the theory that hacked routers are incorporated into a mesh network with the intention of establishing a “chain of nodes between the main infections and actual command and control.”
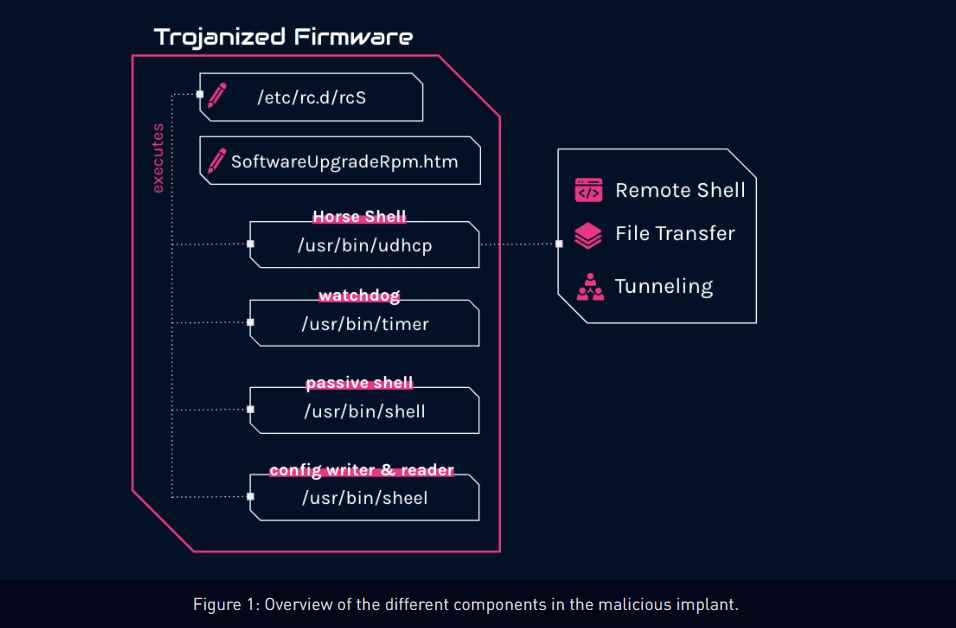
The purpose of relaying communications between infected routers using a SOCKS tunnel is to establish an additional layer of anonymity and disguise the end server. This is achieved by the fact that each node in the chain possesses information only about the nodes that came before and after it in the chain.
In other words, the approaches obfuscate the source and destination of traffic in a way comparable to how TOR works, making it much more difficult to discover the scope of the attack and disrupt it. The finding is just one more illustration of a long-standing pattern in which Chinese threat actors target Internet-facing network equipment to manipulate the underlying software or firmware of such devices.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He has also worked for security companies such as Kaspersky Lab. His daily work includes investigating new malware and cybersecurity incidents. He also has a deep level of knowledge in mobile security and mobile vulnerabilities.
Send news tips to info@noticiasseguridad.com or www.instagram.com/iicsorg/
You can also find us on Telegram www.t.me/noticiasciberseguridad
#Hackers #P2P #network #hacked #TPLink #routers #world #router #part
